All Stories
Opps - no_image
LivelockA thread often acts in response to the action of another thread. If the other thread’s action is also a response to the action of another thread, then livelock may result. As ...
In tutorial, no_image, opps, Jan 23, 2025Opps - no_image
DeadlockDeadlock describes a situation where two or more threads are blocked forever, waiting for each other. Deadlock occurs when multiple threads need the same locks but obtain them...
In tutorial, no_image, opps, Jan 23, 2025Opps - coupling
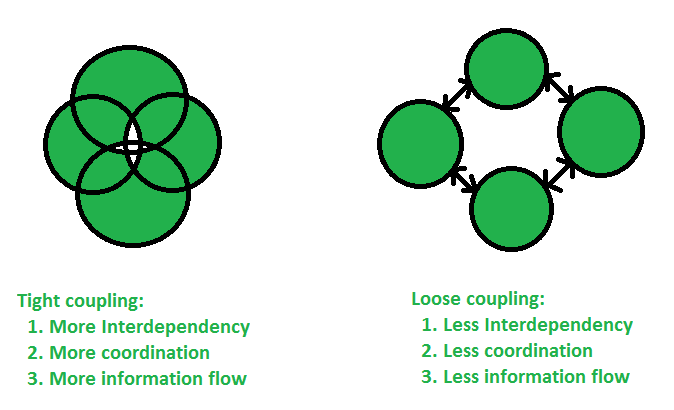
CouplingCoupling is the degree of interdependence between software modules; a measure of how closely connected two routines or modules are; the strength of the relationships between m...
In tutorial, coupling, opps, Jan 23, 2025Opps - cohesion
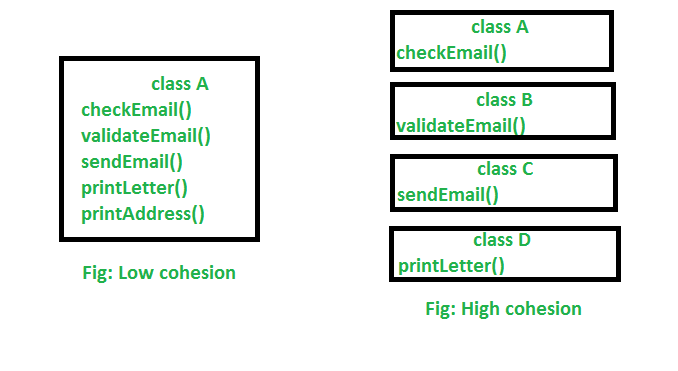
CohesionCohesion refers to the degree to which the elements inside a module belong together. In one sense, it is a measure of the strength of relationship between the methods and data...
In tutorial, cohesion, opps, Jan 23, 2025Opps - no_image
ScrumScrum is an agile project management framework that helps teams structure and manage their work through a set of values, principles, and practices. Much like a rugby team (where ...
In tutorial, no_image, opps, Jan 23, 2025Opps - no_image
REST, or REpresentational State Transfer, is an architectural style for providing standards between computer systems on the web, making it easier for systems to communicate with each ...
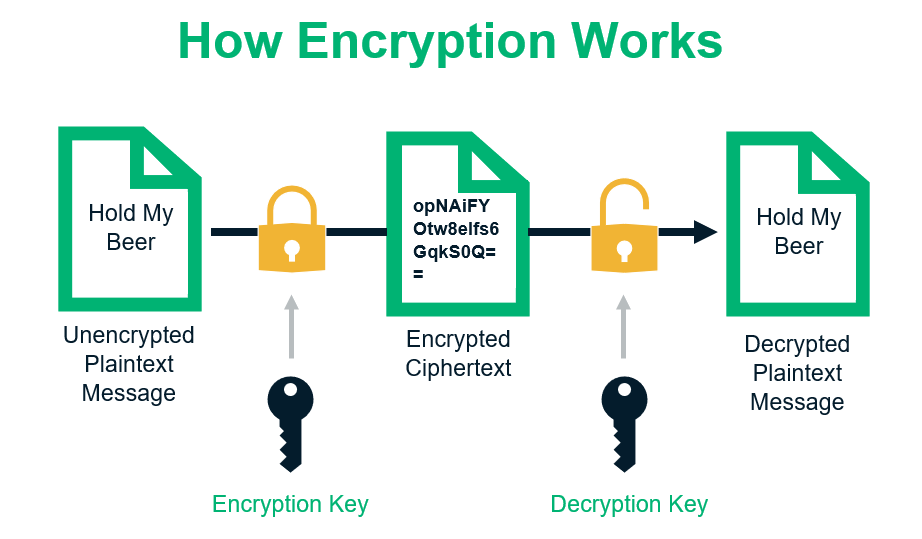
In tutorial, no_image, opps, Jan 23, 2025Opps - man_in_the_middle_attack
Man in the middle attackMan-in-the-middle (MITM) attack is a cyberattack where the attacker secretly relays and possibly alters the communications between two parties who believe that...
In tutorial, man_in_the_middle_attack, opps, Jan 23, 2025Opps - no_image
KanbanKanban is an agile framework used for project and task management. At its core are continuous improvement and just-in-time development, which allows teams to stay on top of any ...
In tutorial, no_image, opps, Jan 23, 2025Opps - fdd
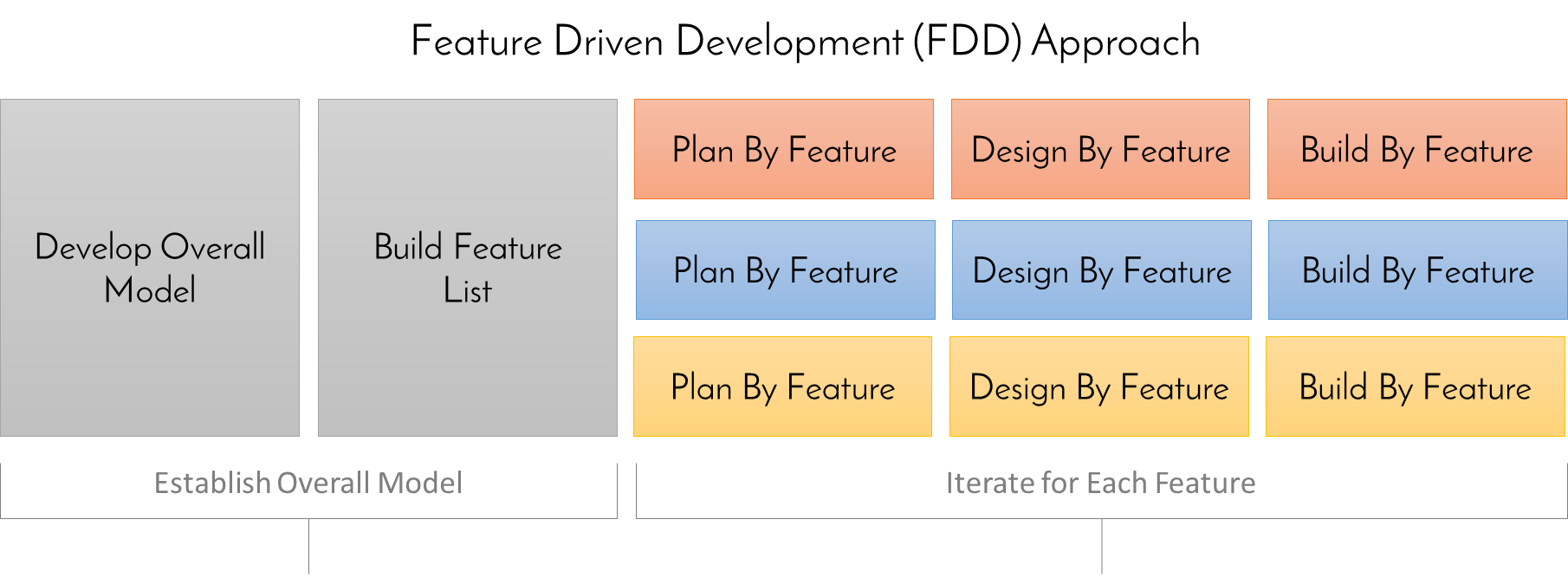
Feature Driven Development (FDD)Feature-driven development (FDD) is an iterative and incremental software development process that follows the principles of the agile manifesto. The i...
In tutorial, fdd, opps, Jan 23, 2025Featured
-
Testing - no_image
In tutorial, no_image, testing, -
Live_Data
In featured, tutorial, android, -
Kt Coroutine
In featured, tutorial, android, -
Flutter interview questions
In Flutter, oneview, -
Hilt DI Deep Dive
In Android, DI,